The legal situation is more complex and nuanced than the headline implies, so the article is worth reading. This adds another ruling to the confusing case history regarding forced biometric unlocking.
Reminder that on an iPhone, if you hold the Volume Up and Power buttons simultaneously for several seconds, the phone will vibrate and will require the PIN or password next time you unlock it, not Face/TouchID. This happens whether the screen is on or off, so you can discretely do it in your pocket.
Or just use pin all the time, no face or fingerprint.
And then some random dude takes a peek at you entering said password, and steals the phone :/
GrapheneOS has an option to scramble the numbers on the unlock screen. I don’t know if that’s a base android thing or available on IOS
Correct. Not sure about iOS either, but many custom roms can, e.g. divestos, probably resurrection remix used to have it back when it was a thing (not sure here, but I distinctly remember having this feature somewhere before graphene)
In order to turn off the Find My iPhone functionality, you need the Apple ID password, so this isn’t even a real concern. You can even remotely lock the phone with a new password. Apple has made stealing an iPhone and making it work afterwards very hard.
The idea is usually to access the victim’s banking app, or 2fa app, etc, AFAIK.
Both of those require their own password or biometrics, so you couldn’t access those either.
Idk about iOS, but android lets you add a fingerprint using the lock screen password
When changing biometric data on the iPhone, it locks you out of using it in other apps, making you put in your bank/other specific password.
Basically every Android also has a variation of this
So you know what it is? I just tried both volume keys and all I got was TalkBack (Google’s screen reader).
it’s called lockdown mode. on my phone you press and hold the power button and select the option. you might have to enable this in settings.
Holy connoli, you are right! I just enabled it.
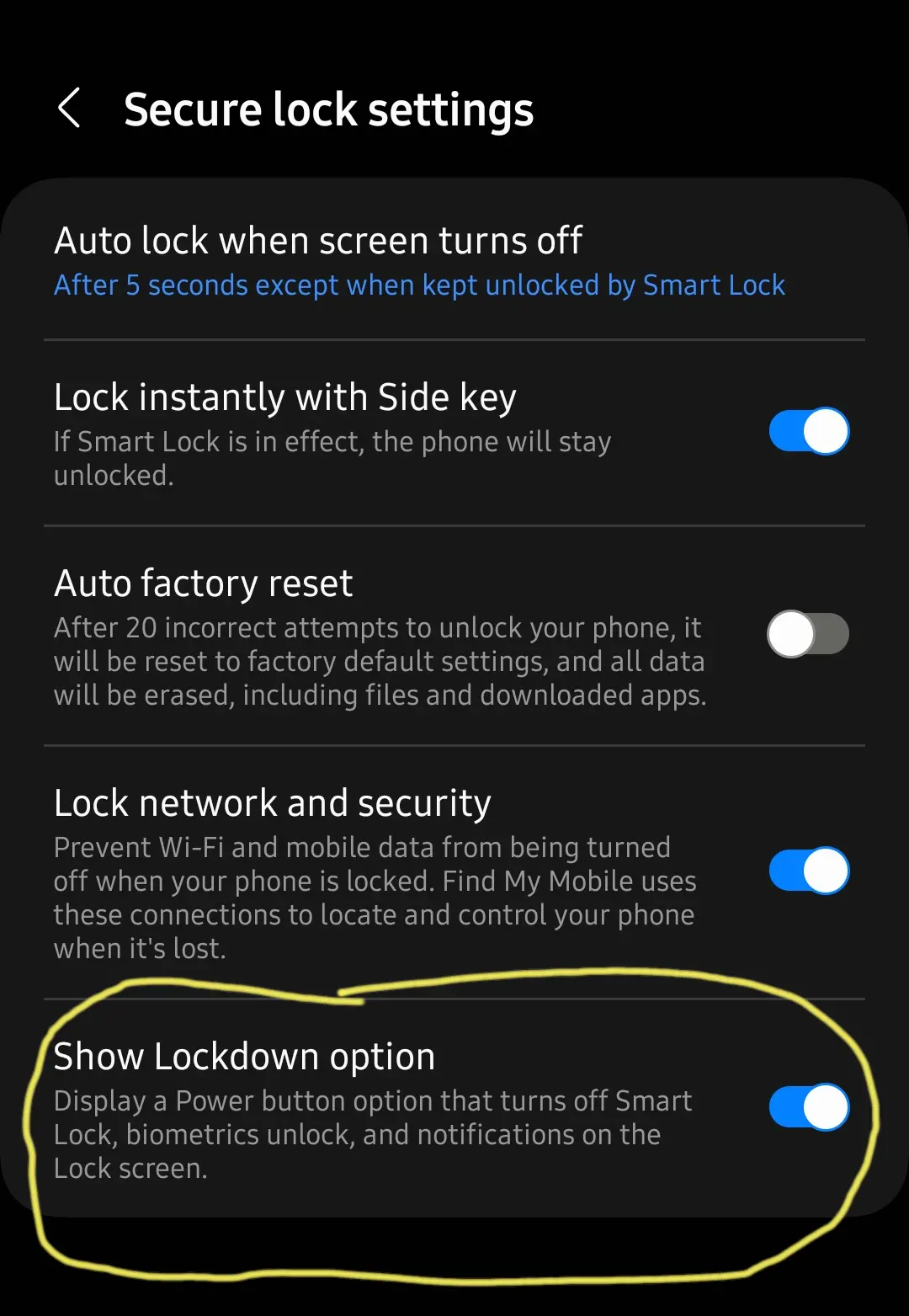
At least on my phone, rebooting also makes it require PIN
Yeah, that’s right. Which is fucking annoying, to be honest.
I find it a little useless since you can also shut it down or force restart (continuously hold power button until it restarts)
Absent an idiotic carrier/mfg skin that disables the feature, you just long-press power then click “lockdown”.
Or reboot the device. Rebooting the device will also leave it encrypted if your device has encryption (the PIN/password is needed to decrypt, essentially).
Nope.
Samsung A50 doesn’t have this option.
Will keep an eye out for it though.
Depends on the rom. It’s in Android since 9. Samsung definitely has it, but you have to enable it
I didn’t realize how many people didn’t know this so someone should probably post a PSA and quick guide in c/Privacy.
My Samsung A11 (android 12) has a “lockdown” option when you held the power button. It would turn off all biometrics and hide notifications. You may have to dig in the settings to enable it, though
If you don’t, just force power restart it. You can search this up online for your model.
https://www.hardreset.info/devices/samsung/samsung-galaxy-a50/softreset-second-method/
You need to enable it. “show lockdown option”
Without having to look at the device?
Nope :(
Not sure about all phone models, but at least with mine, if I switch it off then it requires a PIN, rather than biometrics, upon being switched back on. Thus if the police arrive, immediately switching off your phone could be a sensible thing to do
Restarting phone as well so the same thing
On iPhone, maybe Android too, you click the power button 5 times and you have enter the pin.
On my phone, it gives a 5 second delay before making an SOS call.
Ditto. That gave me quite the fright!
press and hold the lock button and select the option to enter lockdown mode. lockdown mode requires the PIN.
this might be an option in settings if yours does not have it enabled already.
Also, just going to the power off slider screen will force a passcode reentry.
Watch out I guess, because that opens the Emergency SOS page on my OnePlus phone and, if I have an additional setting toggled, automatically phones emergency services… the phone does not lock
This isn’t new. I’ve been on the passcode to unlock train for a long time because of this. It’s only news in that it’s been codified by the court. You can’t be compelled to reveal info.
On iPhone: press and hold the lock button and either volume button for 1-2sec. It’ll force a passcode despite biometrics.
You can also turn your phone off. Phones require a passcode after booting up.
I hate Siri, but you can do a “Hey Siri, whose phone is this?” and it will force PIN unlock. Great if you aren’t able to physically touch the phone.
Or use wrong finger for multiple times untill its locked out with pin password
Careful locking your device before the cops get there. It could be considered tampering with evidence.
Got any evidence to back that up?
Not anymore, they tampered with it
🤣
Source: his arse?
Even then, in his arse, they’d have to prove the person locked it.
But what’s worse, getting a tampering with evidence charge, or giving them everything?
Still would like to see his source.
The source:

In the States police can bust you on false charges and it will typically (but not always) fly in court.
They also have strong phone cracking software, despite what FBI says about piles of evidence locked away in phones.
Evidence is not a thing until you are at least accused of a crime or detained.
That’s not completely true. In most states if they are knocking down your door with a search warrant and you flush a kilo of heroin down the toilet, you’re getting an evidence tampering charge that will hold up in court.
They would have to prove beyond a reasonable doubt that you only flushed it after hearing them knock on the door.
There’s a whole lot of caselaw surrounding this, and they will get someone to destroy the pipes to find out when they were flushed (their word goes, good luck finding someone impartial to say that wasn’t what happened). I wish court cases were built on 1’s and 0’s like computer code but that’s just not the way the world works.
Even if this is true, and I’m not arguing that it isn’t, if you’ve committed a different crime with a worse punishment, you’ll have to take that into consideration.
Makes perfect sense to me (not a lawyer, not a US person)… what doesn’t make sense is how many people still think biometric is high security (maybe because of how cool they make it look in the movies?)
Idk… you being forced to use your body against your will to reveal secret and private things sounds pretty awful to me
Idk… you being forced to use your body against your will to reveal secret and private things sounds pretty awful to me
Hopefully it gets overturned and your compulsion to stick your finger on the devices requires a warrant.
I’m in partial agreement with @gomp@lemmy.ml, they should be allowed to take your fingerprint and then apply that fingerprint to a device. Or get a warrant to make you stick you finger on the device. Recording your fingerprint is just collecting data to investigate a crime, it generates a record. Sticking your finger on a device is making you participate in the investigation, and generates no investigative record other than “device did/didn’t unlock”.
If the popo suspect you killed your wife and find you sitting on top of a chest freezer refusing to come off, should they be allowed to force you?
Not without a search warrant.
And what if it’s the trunk of his car?
Which better relates to the case in the OP, as the lack of a search warrant was never the question here:
Payne conceded that “the use of biometrics to open an electronic device is akin to providing a physical key to a safe” but argued it is still a testimonial act because it “simultaneously confirm[s] ownership and authentication of its contents,” the court said. “However, Payne was never compelled to acknowledge the existence of any incriminating information. He merely had to provide access to a source of potential information.”
Biometric is high security against thieves and nosy girlfriends, not kidnappers or cops apparently. You need to be physically present for most of them which means it can’t be done without you knowing. The problem arises when the person who wants access also has access to you.
Also not a lawyer or a US person, but from listening to American tech media, this has been an issue of some debate for a decade or more now.
The trick lies in their 5th amendment right against self-incrimination. Police cannot require you to give your PIN because that would violate 5th amendment rights. It has been ruled in some parts of America (but the ruling in other parts has been the opposite, IIRC) that you can be forced to give biometric unlocks. In my opinion this is kinda silly and inconsistent. It might be in line with the letter of the law, but it’s certainly not in keeping with its spirit.
As an American and avid rights understander, it is not the 5th Amendment which this risks violating (which you did cite correctly), but the 4th Amendment, which guarantees protection from undue searches and seizures of your person, property, or effects. This is the whole reason for the warrant requirement and the reason you hear us bitching whenever something comes up that lets police or agents of the government acquire non-public access to information or property in a warrantless way.
An example: the police are investigating Mary’s death and suspect you of having planned the murder in the Notes app on your phone, so they want to get into your phone. Without a court order (warrant), you have to give them permission. With the court order, you must give the passcode and/or unlock the phone.
Now, at this point, if your passcode happened to be ‘I killed John02&’ you could argue 5th Amendment protection because divulging the information would incriminate yourself in the crime, or a different crime.
I believe the reason the 5th is usually referenced is that this usually comes up in situations where the 4th is already not relevant. Either because there already is a warrant, or because you’re crossing a border (which IMO seems like an incredibly sketchy excuse and would likely not have been accepted by those who originally penned the 4th amendment, but is at least well-established law at this point).
With the court order, you must give the passcode and/or unlock the phone
The thing is, case law has determined that this is not the case. Passcodes are fairly well protected, from what I’ve heard. You cannot be made to divulge them anywhere in the US, because of the 5th amendment, even with a warrant. Case law is more split on whether biometrics should be offered the same protection.
Though again, this is all my understanding of it having heard it third hand from Americans. Mostly from Americans who themselves are not legal experts, though I think I’ve at least a couple of times heard it directly from lawyers.
They will try to scare you into unlocking your device. I would get a lawyer if you get arrested.
The bigger problem IMO is that the Constitution does not universally apply at or within 100 miles of a border, which is where apparently 72% of the population lives.
Yeah, it’s like if you kept a bunch of illegal things in a safe the authorities have the authority to force you to unlock the safe.
Authorities with a warrant can drill into a safe to get to its contents. That’s legally distinct from forcing someone to unlock the safe by entering the combination. It takes some mental effort to enter a combination, so it counts as “testimony”, and in the USA people can’t be forced to testify against themselves.
The parallel in US law is that people can be forced to unlock a phone using biometrics, but they can’t be forced to unlock a phone by entering a passcode. The absurd part here is that the actions have the same effect, but one of them can be compelled and the other cannot.
It’ll be interesting to see if it applies to facial recognition. In iOS, at least, you need to look at the phone to unlock it. That’s an intentional action. If you look to the side or close your eyes, it won’t work.
So if you’re conscious, you can’t easily be forced to unlock the phone with your face and eyes if you’re able to resist. But if you’re unconscious, then maybe they could use your face (assuming your eyes aren’t rolled back into your head because the cops gave you brain damage.)
But you can be easily tricked. Even easier than with the fingerprint.
“Hey, can you look at those pictures?”, shows some printed out pictures with the phone hiding behind and then quickly just dropping the pictures.
then quickly just dropping the pictures
Could even poke a camera-sized hole in the picture. And disguise it by putting that hole over something similarly-coloured.
But anyway, but of it is really that you can be held in contempt for refusing to unlock with biometrics, if they’ve got an appropriate warrant.
Probably a “have a look at this” and the 2 seconds before you realize that you are currently unlocking your phone, would be enough.
They can also compel you to provide a key to the safe, should one exist.
The issue constantly is something you have vs something you know. They also can compel you to provide a document or item from within the safe, if they know that the item exists.
Depends on the country you life in. And even in the USA it is to my knowledge not correct. They can try to crack it themself but you have not to comply.
Nobody cares. It’s easy. Folks aren’t out getting arrested in mass, even in the United States. Unless youre out selling drugs or protesting while breaking shit it has no functional effect on your life in any way.
Ah, yes, if you’ve done nothing wrong argument.
I still care whether government is being properly restrained in applying it’s power against any individual citizen, because that citizen represents all of us.
Innocent until proven guilty, and all that
I don’t care. I’m just saying the why.
TBH privacy advocates have largely put themselves into the position of the window ME UAC prompt. They are deaf to it and IMO it’s a large part of the privacy community treating everything like an 11 and refusal to look towards a user friendly threat model.
Enter pin
“I don’t know what happened, it’s the right code, might be broken.”
That pin was device self sanitiziation trigger for preventing information from falling in the hands of the enemy.
Then buy enough claymores to make sure there will not be a second encounter with enemy forces.
I really wish the GrapheneOS devs would add duress passwords…
Not as part of core GrapheneOS, but an app called “Private Lock” can detect sudden force via accelerometer and disable the fingerprint based unlocking for next unlock.
But yeah, an erase passcode feature with opening a decoy profile would be a great feature to have.
E: grammar
That’s exactly right, I and it works like a charm.
A duress password to remove selected profiles would be amazing. So it still unlocks but quietly removes the profiles you are worried about.
Not even remove them, honestly. Just unlock the phone into a sanitized, honeypot account that has no access to the secured accounts contents!
If you do go digging you would get caught. Safest way is removal in those situations. I rather have some data removed which preferably I have backups up. Then have to risk jail time in some country.
For iphone brothers and sisters (courtsey of rpcameron)
You must be using an Android device. On the iPhone, 5 quick presses of the side/power button (or long-pressing power+volume) will bring up the Power Off/SOS menu; any future attempt to unlock will require the passcode. (Either action can be down without any screen interaction, meaning that you can enable this feature silently as soon as you feel it necessary.)
(Also to note for iPhones: if you choose a 7 digit or longer passcode, the entry field does not indicate how long the passcode is; the same is true if you choose an alphanumeric passcode.)
(Extra safety for those in the US if you are in a car, after doing the above stash your phone in the console/glove box; if it is within a sealed compartment not on your person additional cause/warrant is required to gain access to the device.)
Another benefit to this is that the USB port goes into a restricted mode that only allows for charging, and you can still use your cameras to record while it’s in this mode.
Memorize and practice this! You can do it in 2 seconds.
you could also just do basically the same thing with Android, but instead of locking it you just turn it off and it’ll be locked the same way when turned back on.
A number of Android phones support most of this functionality. Unfortunately, you have to actually click on a “Lockdown mode” button after long pressing power+volume-up. Hopefully Google catches up here.
This may be the first time a federal ruling has been made but I don’t know if it applies to state crimes. Many counties across the nation have ruled one way or another.
SCOTUS once ruled law enforcemeny cannot compel you to unlock a device at all and cannot access your phone without a warrant, but I don’t know if that is current. Police can legally lie to you (and beat you with a $5 wrench and pronably get away with it in court).
They also have strong phone cracking packages despite FBI’s lament about evidence locked away in seized devices.
Generally, do not consent to searches or cooperate without a lawyer present. Expect everything an officer tells you is intended to mislead. They will even lie in court to the judge.
First order of business: never enable the thumbprint lock on your phone.
Second order of business: never conduct any sensitive business or communication with a mobile phone.
Third order of business: use a very strong passphrase to lock your phone.
Fourth order of business: understand that all your phone calls and text messages are hoovered up into spook databases.
This is one of many reasons you should use a password of some kind that you keep inside of your head to unlock your phone rather than a biometric that people can use to unlock it against your will.
Or just use lockdown mode in android to force phone to only unlock with password
How is that different from the usual way of having a password as your way of accessing your phone?
lockdown mode is a button that comes up with the power menu. they mean turn it on when you’re pulled over or whatever
Logically, seems less safe
Practically, I DO miss unlocking the screen with my thumb 🤣
Its temporary. Just something you can quickly switch on in case of an interaction.
Use. Lockdown. On. Your. Phones. It is easy and prevents legal shitbags from literally forcing your hand.
I just wish you could setup logic for this. Pulling out your phone to hold the power button for 3 seconds and then tapping the lockdown button is slow, very obvious, and likely to be prevented by an attacker.
Would be great if I could set it up to lockdown on a specific finger, or a specific number of presses on an analog button. Or even like if I leave a WiFi network or some other arbitrary condition.
This article and similar threads keeps popping up in my feed, so I’m going to keep spreading this tip around. (I’m using Android.)
I use tasker to automatically lockdown my phone based on accelerometer and Bluetooth. A sharp tap to my phone or being disconnected from Bluetooth is enough to lockdown my phone and disable all biometric access. I dialed in the sensitivity so that it doesn’t take much, just a tap on my pocket, being set down a little too aggressively, pulled from my car and thrown to the ground is all it takes. I set it to notify me with a quick vibrate when it does this for a little added confidence that it is behaving as expected.
For a little added effort I can have tasker snap a photo that gets backed up to the cloud any time there is a failed unlock attempt, just be prepared for some unflattering photos of yourself looking like an aging male boomer posting selfies to the facebook.
Do you mind share it?
deleted by creator
Will check it out, thanks for the tip.
EDIT: It’s closed source, $4/license with a 7-day free trial.
I like using a specific finger. Guess which one wed all pick 😂
Lol.
I’m right handed… But I almost always use my left index to unlock, so that’s what’s set.
Be funny to watch police force me to use my right index…
Hmm, is there an app/feature where if I use my thumb-print instead of say, my fore-finger print, it wipes the phone instead?
I looked into it a few years ago. Eg left thumb locks biometrics and requires pw (thus saving you from this particular law) . Right thumb just unlocks like normal.
Back then it was impossible, because biometrics couldn’t differentiate between fingerprints for lord knows which security reason.
No idea if there is a solution for this already, but imo it would be a very important security feature.
Tasker does this on android and the event can be chained to launch scripts and apps.
deleted by creator
This is the best summary I could come up with:
The US Constitution’s Fifth Amendment protection against self-incrimination does not prohibit police officers from forcing a suspect to unlock a phone with a thumbprint scan, a federal appeals court ruled yesterday.
The ruling does not apply to all cases in which biometrics are used to unlock an electronic device but is a significant decision in an unsettled area of the law.
Judges rejected his claim, holding “that the compelled use of Payne’s thumb to unlock his phone (which he had already identified for the officers) required no cognitive exertion, placing it firmly in the same category as a blood draw or fingerprint taken at booking.”
Payne conceded that “the use of biometrics to open an electronic device is akin to providing a physical key to a safe” but argued it is still a testimonial act because it “simultaneously confirm[s] ownership and authentication of its contents,” the court said.
The Supreme Court “held that this was not a testimonial production, reasoning that the signing of the forms related no information about existence, control, or authenticity of the records that the bank could ultimately be forced to produce,” the 9th Circuit said.
The Court held that this act of production was of a fundamentally different kind than that at issue in Doe because it was “unquestionably necessary for respondent to make extensive use of ‘the contents of his own mind’ in identifying the hundreds of documents responsive to the requests in the subpoena.”
The original article contains 662 words, the summary contains 241 words. Saved 64%. I’m a bot and I’m open source!
People who demand constant internet connect when thy go out have a higher probability of having too much personal information on their phone. It’s a difference in mindset or mentality.
Cell service is overrated. Given the amount of people in public that are either scrolling or on some form of a social media shows having data service is not as important as people think it is. I have a GrapheneOS phone for listening to music and if I want to check for public wi-fi for a specific task but most days I never connect online when I am out and I’ve never signed up for a cell data plan before.
Life can be happier when someone is out in public and can’t check messages, that usually can wait anyways for a few hours, and they can enjoy the world around, not what’s on a screen.
I don’t believe doing things over public WiFi is that secure as traffic can be logged etc.
Most traffic these days goes over secure channels. Any time the website you’re accessing is HTTPS, they can see that you’re accessing that website, but they can’t see which pages you’re on our read what they say, or what you submit.
The exception is if they get you to install their own certificate to allow them to man-in-the-middle you. Laws in some authoritarian countries already require devices have root certificates that allow the government to spy on everything. And the EU is currently considering the same. Which should be a major concern for any European residents.
With a new randon MAC address created each time it connects online, logging means nothing for trying to identity or remembering a device.
???

This has been a theory for a while, just not sure it was a specifically ruled precedent. The notion being similar to how they can force fingerprinting but not testimony. Access to a physical lock or location you can’t simply say ‘stay out’ but they can’t force you to divulge a password since it’s a thought in your mind.
Also, relying on biometrics is terrible, quick but immutable keys are a big no-no.
Eh, I never stopped using a password for this exact reason.
I think this solution is way too impractical for most people, who tend to unlock their phone many times a day.
Yeah, that’s the cost of good security practices. You always sacrifice convenience.
I wish I could have a fingerprint and a pin with a limited number of attempts. Plus a password after like three failed pin attempts. I think that would be a pretty good balance between security and convenience.
I mean, it is annoying. But it’s security. Don’t want people having access to your device, remove all possibility someone CAN.
But it is annoying, we shouldn’t HAVE to do this. Privacy should be baked right into our daily lives and not clawed out with tired hands every chance we get.
Yeah. The huge legal distinctions between different ways of unlocking a device seem absurd. Comprehensive privacy legislation would help.
deleted by creator